Governance, Risk & Compliance:
Consistency Keeps Agency Data Secure

CLICK ON ICON TO SEE PROJECT COMPONENT
POLL REVEALS HALF OF GOVERNMENT AGENCIES DO NOT ADDRESS NETWORK VULNERABILITIES PROACTIVELY
A new poll sponsored by Dell Software reveals half of government agencies do not address network vulnerabilities proactively, impacting security compliance and the ability to respond to threats.
With federal IT departments stretched thin, how many days has it been since you last verified meeting internal policies, backed up your data, or monitored your environment to see who has access to what and whether they’ve done anything with that access?
IF THE ANSWER IS MORE THAN ONE HOUR YOU MAY RUN THE RISK OF:
- Failing an audit
- Non-compliance with new mandates
- Inability to provide evidence of data to satisfy legal requests
- Inability to respond to a request from senior management, HR, or finance for a report
- A data breach threat
- Loss of critical data
When it comes to data security, it’s not a matter of IF something will go wrong, but WHEN. Is your agency prepared?
Fill out the form below to download the study results white paper, which details top federal IT compliance and governance concerns, potential costs of non-compliance and key attributes of audit and compliance solutions.
Fill out the form below to download the research report and white paper.
Governance, Risk & Compliance:
Consistency Keeps Agency Data Secure
YOU WILL LEARN:
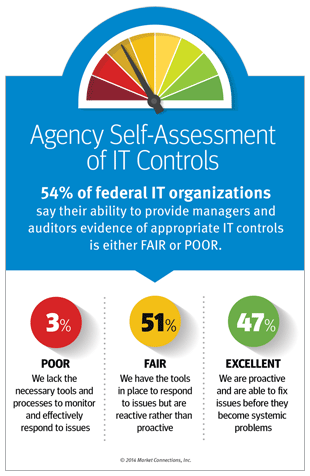
- How federal IT organizations rate their ability to provide managers and auditors evidence of appropriate IT controls The differences between “reactive” and “proactive” IT organizations when it comes to data and systems governance, risk and compliance
- Key attributes of governance, risk and compliance solutions
